Cloud service and data security
RS Production is delivered as a cloud service and uses Microsoft Azure as a cloud provider. All infrastructure is running on Microsoft Azure.
Microsoft Azure complies with the following certifications http://azure.microsoft.com/en-us/support/trust-center/compliance/
Setup
Describes the current configuration/deployment of the RS Production cloud service in Azure. The current configuration is checked and maintained using Microsoft Defender for Cloud.
Azure deployment overview
A logical view of the current deployment
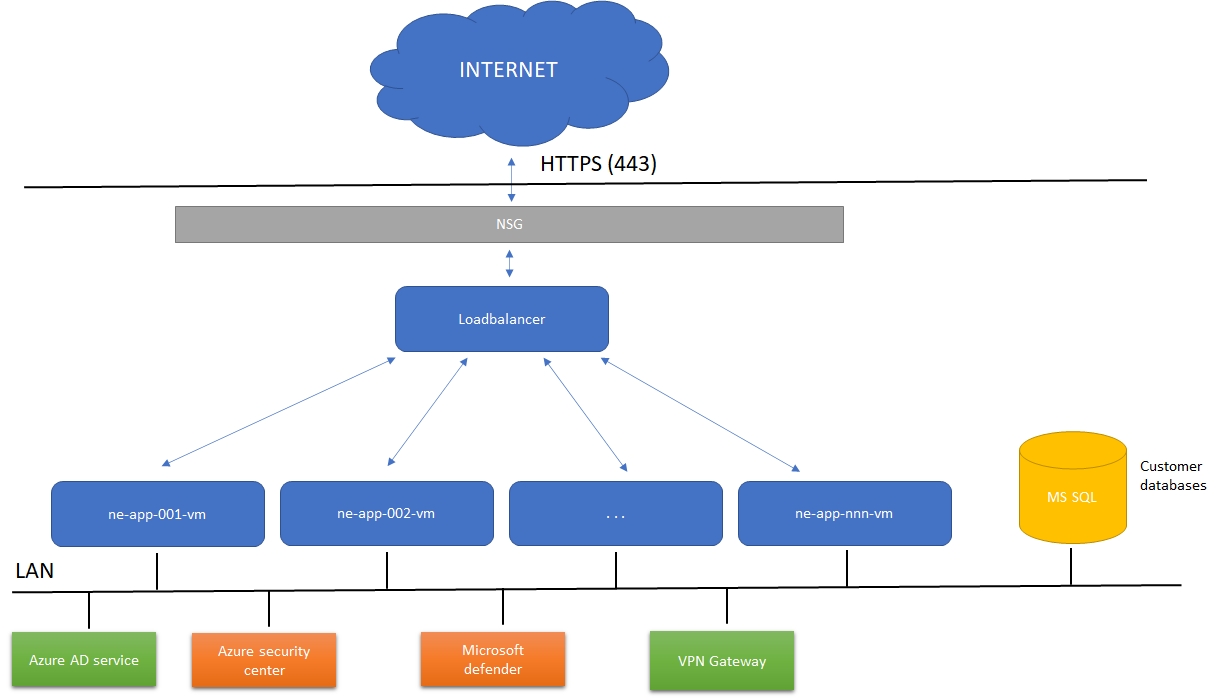
The application servers are reached through standard protocols using HTTPS (with Transport Layer Security, TLS).
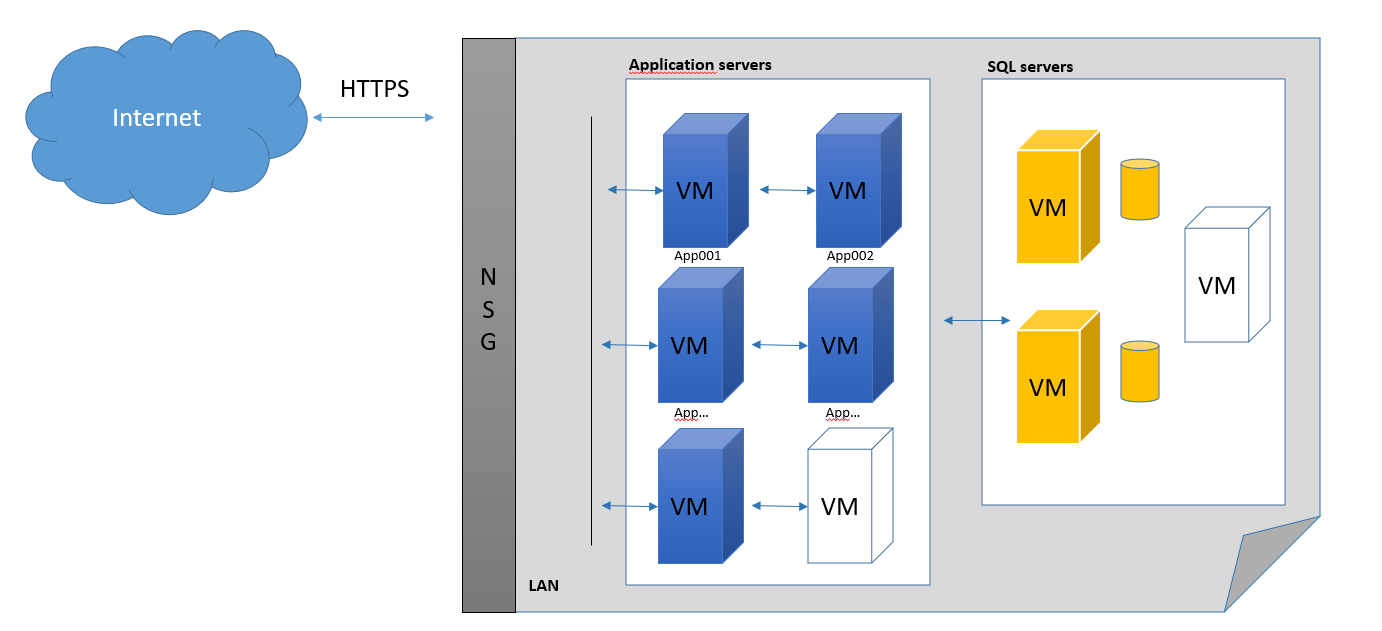
Each customer has a Windows service running on the application server.
All data is stored in SQL Server, one database per customer.
Application servers
Responsibility: Host RS-Production service (server software), communicates with clients through HTTPS.
Database servers
Responsibility: Host Microsoft SQL Server. Communicates with the application server over private LAN, no public ports open to the Internet, all communication between app servers and database servers on internal LAN in Azure.
Database isolation
Every installation is fully isolated in its database. It means that two customers’ data is never stored in the same database.
Customer-to-Azure communication
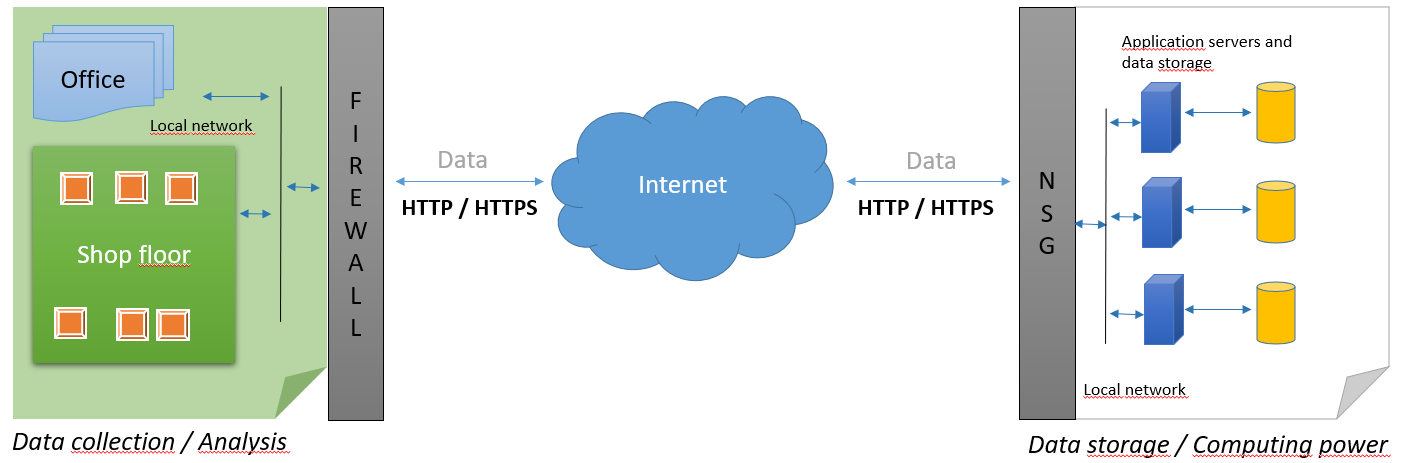
The factory needs to allow outgoing HTTPS (443) traffic in its firewall to connect to the cloud service.
RS IoT devices communicate through MQTTS (8883) (Secure/Encrypted MQTT).
RS Production mobile app communicates over HTTPS.
Resilience
The standalone client works without an active connection to the server. The operators can still work using the operator panels in production even if there is no active connection; all data is stored locally until the connection is reestablished, then all data is synced with the server.
No data loss if the connection to the server is lost
The client syncs all data when the server is up and running again
Backups
Server infrastructure
All servers are backed up with daily image snapshots with 7 days retention.
Databases
Full backups twice a day.
Transaction log every hour.
Stored on a separate disc.
Patching
Critical and security OS patches are performed every week.
All server patching is done accordingly to alerts and recommendations from the Azure security center. The Azure security center alerts when a critical or security update has been published. Read more about Azure Security Center under 4. Security.
Security
For cloud security, hardening, and policies, Microsoft Defender for Cloud is used. Microsoft Defender for Cloud gives recommendations and insights about current threats, configurations, and patching.
Security incidents
If an event may indicate that the measures put in place to protect the RS Cloud service have failed, or RS and data have been compromised. An incident report will be compiled and sent to the customer’s Security contact or Support contact registered in the support system.
Identity access management
Remote access
All administrative access is through VPN.
Personal information and data pruning
The only personal data that RS Production stores is the RS Production user profile. The user profile data has mandatory fields for username and password. The RS Production user accounts are handled by each customer and can be easily deleted.
If a user account is deleted, all history of the personal data will be erased after the database backup retention time has expired, which currently is 14 days (snapshot + file backup).
RS Production
Passwords are encrypted in each customer database
Customer databases and database backups are encrypted at rest using: https://learn.microsoft.com/en-us/sql/relational-databases/security/encryption/transparent-data-encryption?view=sql-server-ver17.
Support
The standard procedure when communicating with our support, there are four escalation levels
4: Affects production (all resources, incl. the development team)
This can occur when RS Production is highly integrated with the ERP system
3: Possible data loss (development team, if support needs assistance)
Possible cause: the system is incorrectly configured
2: Data visualization (development team, if support needs assistance)
The outcome of the system shows incorrect data (an error in the calculation), but the underlying data is correct.
1: Normal
System administration, basic training
All support cases are rated according to the table above and registered as new support cases in the support system. The above is the standard procedure for special handling and SLA; see your specific support contract.
Technologies
RS Production
Both the client and server are built using the .NET Framework.
Code signing
All executables are digitally signed using a code-sign certificate.